Speaks About: Passwords
I know that this won’t surprise you, but internet security is hard.
It doesn’t surprise you because you, my dear Reader, are consuming this knowledge on the internet right now.
[Unless you are Donald Trump, who has his staff print news articles from the internet (concerning him) each morning so he can read them. (“The Mystifying Triumph of Hope Hicks, Donald Trump’s Right-Hand Woman”). But since this entry is not about candidates for president who have been TV hosts, it’s unlikely to be printed.]
And since you are a savvy user of the internet, you have accounts. And passwords. And if you have passwords, then you manage passwords. And you manage them in two general methods:
PROBLEMATIC: You have a password. Or two. Or three. You use them everywhere because remembering passwords is hard or unprofitable brain work.
BETTER: You have lots of passwords, ideally a distinct one for every login. You have the brain juice of a god, because the average person has at least a dozen accounts if not multiple dozens. Your passwords are one-location-use only. And you devise new passwords at regular intervals, never reusing any.
If you are in the BETTER group, cheers! I don’t have anything to say to you about passwords. Feel free to read on for the jokes, otherwise you can come back next semester for my session on two-factor.
But if you fail from the BETTER group in even a single degree, such as “I reuse some passwords,” or “I don’t memorize, I write down,” or “I don’t change my passwords,” then we need to talk.
The problem with passwords? We humans do them poorly. And intruders are great at them! We often conceive of passwords as information that will be more secure if the information is less known. A security-inexperienced person thinks “I wouldn’t use my first name as a password! Everybody knows that. But my mom’s name…”
The problem isn’t that the password needs to be obscure. Obscure data might discourage another human from GUESSING your password, but the person trying to hack your email is unlikely to be guessing. They may be using brute force, which is computer-assisted. The computer will begin: 1 *fail* 2 *fail* 3 *fail* and so on. It may also try: a *fail* ab *fail* abc *fail*
You might say, “That will take forever!” But don’t be confused. Computers are designed to do lots of simple things very fast.
Let me take the opportunity to direct you to a fun and illustrative site,
This site does a great job of showing you how passwords look to computers. Let’s put in a few passwords for show.
- “Jab” -- A simple word fares quite a bit better: 400 nanoseconds. A nanosecond is a billionth of a second, orders of magnitude slower. But it still could try (and match) a million of such before you finish blinking.
- “Jabx” -- A simple word with a suffix. Takes 11 microseconds, or 11 millionths of a second. We’re getting better and better!
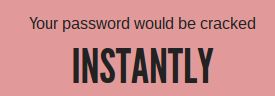
- “Butter” -- Since longer words seem to take longer, let’s use a longer word. Except, oh no and woe! This password is SO easy to crack we’ve been downgraded to “instantly.” The page helpfully tells us that not only is it “possibly a word” and therefore subject to a dictionary attack, but “butter” is in the top 250 most-used passwords, so is likely to be tried first. Butter is good for cooking, but an abjectly disastrous password.
- “lkihu,ukh,i,h” -- So I put my fist down on my keyboard and rocked it back and forth. It would take 2,000 years! Not bad. Not in any dictionary, check. But it’s a little hard to memorize. If I had two-dozen passwords like this and could keep them straight, I probably wouldn’t have enough brain left to chew gum.
It turns out that the primary thing for increasing password strength is the number of characters. Longer passwords are better than more diverse passwords (short passwords with symbols, capitals, numbers, etc.).
A great cartoon on this subject from xkcd.com:
https://xkcd.com/936/
So, let’s make a wordy password! How about “ArmisticeGlobulePerspicacitySolemnizes”? Turns out it’s 128 quattuordecillion years. That’s 128 followed by 47 zeroes. Or 12,800,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000 years. That’s so long that I’m not even sure I counted the zeroes correctly. But even that would be dwarfed by a string of gibberish that long.
Good thing it’s largely irrelevant.
*** *** ***
As interesting as all this stuff about passwords is, internet security has moved on a bit from this. It’s impractical for someone to set up a server and try to brute force your Gmail password. One of the most effective ways to circumvent brute force is to throttle the inputs. Have you ever forgotten a password a few times in a row, and then had a time limit placed on you before you can try again? It’s not just to frustrate you, or force you to see if you can research your password better. It’s to prevent brute forcing.
If my nefarious computer can guess 10 billion passwords a second, it doesn’t matter if the system on the receiving end can only take five guesses before it forces me to wait 1 minute before guessing again. Now I only get to make a thousand inputs per day. And if I trip the throttle alarm and still input wrong answers for days on end, eventually they’ll ban my IP address. Another wall.
And on the flip side, we can have better security than just a password. A one-in-a-quattuordecillion chance could still happen five minutes from now. That’s not an acceptable risk for your banking information. Or the launch codes for a nuclear missile.
Are strong passwords still important? Yes. Much of the internet still runs on password-only authorization. And for those things, it’s still very important to have strong and non-duplicated passwords. That slows access to one account, and prevents having one breach cascade through your entire online portfolio.
Password manager programs like OnePass and LastPass help. They allow you to create complicated passwords easily, easily update passwords, and act as a digital locker. They’re also scary, because anyone who gets access now has access to all accounts.
It’s too much power to secure behind a single password, no matter how complex. So what happens?
Tune in next time for the multi-authentication tango.



Comments
Post a Comment